In the competitive landscape of cybersecurity recruitment, identifying skilled professionals who can handle real-world threats is paramount. Parrot CTF’s Enterprise Candidate Processing system revolutionizes how organizations assess, evaluate, and onboard cybersecurity talent through practical, challenge-based evaluation.

The Challenge with Traditional Hiring
Traditional technical interviews often fall short in cybersecurity recruitment. Resume screening and theoretical questions don’t accurately reflect a candidate’s ability to identify vulnerabilities, respond to incidents, or think like an attacker. Organizations need a way to see candidates in action, solving real problems under realistic conditions.
Enter Parrot CTF Enterprise
Parrot CTF Enterprise transforms the hiring process by integrating Capture The Flag (CTF) challenges directly into candidate evaluation workflows. Rather than relying solely on credentials and interview performance, companies can observe candidates solving actual cybersecurity challenges that mirror on-the-job scenarios.
How the Processing Pipeline Works
1. Challenge Deployment and Customization
The system begins with challenge deployment. Organizations can select from three primary machine types that mirror real-world security scenarios:
Web Application Machines: Candidates assess vulnerable web applications with realistic flaws like SQL injection, XSS, authentication bypasses, CSRF, insecure deserialization, and business logic vulnerabilities. These machines simulate modern web stacks including REST APIs, single-page applications, and microservices architectures.
Network Pentesting Machines: These environments replicate corporate network infrastructures where candidates perform reconnaissance, vulnerability scanning, exploitation, privilege escalation, and lateral movement. Candidates work with firewalls, Active Directory environments, network services, and multi-host scenarios that require pivoting and tunneling techniques.
Reverse Engineering Machines: Candidates analyze compiled binaries, malware samples, or obfuscated code to understand functionality, identify vulnerabilities, or extract critical information. These challenges assess skills in disassembly, debugging, decompilation, and understanding low-level system behavior.
Organizations can also:
- Mix and match machine types to create comprehensive assessment paths
- Create custom machines specific to their tech stack and security needs
- Configure difficulty levels appropriate to the role (junior, mid-level, senior, specialist)
- Set time constraints and scoring parameters aligned with role expectations
Each machine environment is fully containerized and isolated, ensuring candidates have a clean, consistent testing environment while maintaining strict security boundaries between assessments.
2. Candidate Invitation and Onboarding
Once challenges are configured, the candidate processing begins:
Invitation Phase: Candidates receive the event url with clear instructions, time expectations, and access credentials. The system supports single sign-on (SSO) integration for seamless access.
Example: https://parrot-ctfs.com/events/ctf/836372
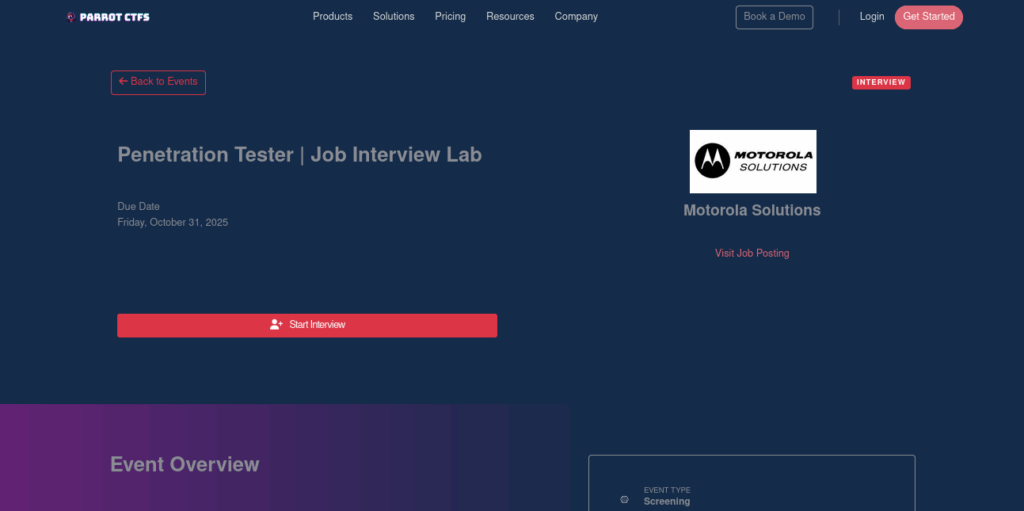
Environment Provisioning: Upon acceptance, the platform automatically provisions dedicated machine environments based on the assessment requirements. Each candidate gets isolated infrastructure, preventing any cross-contamination or cheating concerns.
Machine Types in Detail
Web Application Machines
Web app machines present candidates with vulnerable web applications that mirror real-world scenarios organizations face daily. Candidates might encounter:
- Modern JavaScript frameworks with client-side vulnerabilities
- API endpoints with authentication and authorization flaws
- Database-backed applications vulnerable to injection attacks
- Session management issues and token-based authentication bypasses
- File upload vulnerabilities and server-side request forgery (SSRF)
These assessments reveal not just if candidates can use automated scanning tools, but whether they understand web architecture deeply enough to manually identify and exploit complex, chained vulnerabilities.
Network Pentesting Machines
Network machines simulate enterprise environments with multiple interconnected systems. Candidates demonstrate their ability to:
- Perform comprehensive network reconnaissance and enumeration
- Identify and exploit vulnerable network services
- Navigate Active Directory environments and Kerberos authentication
- Execute privilege escalation on Windows and Linux systems
- Perform lateral movement across network segments
- Maintain persistence and cover tracks appropriately
These scenarios assess whether candidates can think like real attackers, moving beyond single-host exploitation to understanding how breaches propagate through networked environments.
Reverse Engineering Machines
Reverse engineering machines challenge candidates to analyze compiled code without source access. Scenarios include:
- Analyzing Windows PE or Linux ELF binaries for vulnerabilities
- Reverse engineering proprietary protocols or file formats
- Deobfuscating malware to understand behavior and indicators of compromise
- Identifying anti-debugging and anti-analysis techniques
- Extracting cryptographic keys or sensitive algorithms from compiled code
- Analyzing firmware or embedded system binaries
These assessments identify candidates who can understand systems at the lowest levels—critical for malware analysis, vulnerability research, and advanced threat hunting roles.
Orientation: Candidates receive a brief walkthrough of the platform interface, submission process, and available tools. This ensures the assessment measures security skills, not platform familiarity.
3. Live Challenge Execution
During the assessment phase, several sophisticated features activate:
Real-Time Monitoring: Hiring teams can observe progress without interrupting candidates. The system tracks metrics like:
- Time spent on each machine or vulnerability category
- Approach methodologies (tools used, techniques attempted, attack vectors explored)
- Partial progress indicators (services enumerated, vulnerabilities identified, exploitation attempts)
- Resource utilization and tool efficiency
- Hint utilization (if enabled)
Machine-Specific Insights: The platform provides specialized monitoring for each machine type:
- Web App Machines: Track HTTP requests, parameter fuzzing attempts, and vulnerability scanner usage
- Network Machines: Monitor port scanning activity, service enumeration, and lateral movement attempts
- Reverse Engineering: Observe debugger usage, decompiler queries, and analysis tool interactions
Dynamic Difficulty Adjustment: For longer assessments, the platform can adapt machine complexity based on candidate performance, ensuring both struggling and advanced candidates remain appropriately challenged.
Integrity Verification: Built-in proctoring features (configurable based on company policy) help maintain assessment integrity through browser lockdown, activity monitoring, and anomaly detection.
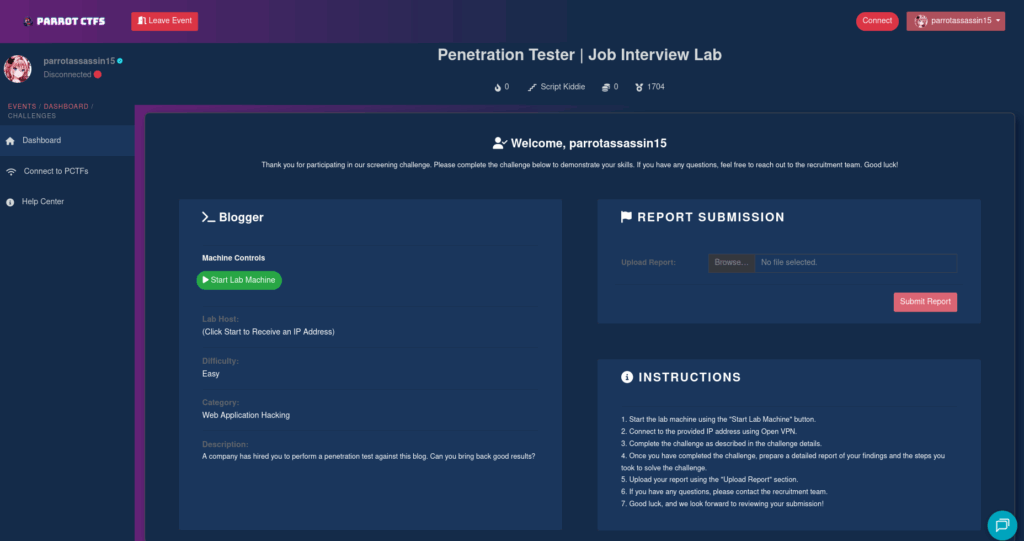
4. Report Upload and Evaluation
Parrot CTF Enterprise takes a report-based approach that mirrors real-world security work:
Comprehensive Report Submission: Rather than simple flag captures, candidates upload detailed security reports documenting their findings. This includes:
- Identified vulnerabilities and their severity
- Step-by-step exploitation methodology
- Evidence and proof-of-concept demonstrations
- Remediation recommendations
- Impact analysis
Real-World Skill Assessment: This report-based system evaluates candidates on the complete security lifecycle;not just finding vulnerabilities, but communicating them effectively. This is critical since security professionals must regularly brief technical and non-technical stakeholders.
Structured Evaluation Framework: Reports are assessed across multiple dimensions:
- Technical accuracy of findings
- Completeness of vulnerability identification
- Quality of documentation and clarity
- Professionalism and structure
- Actionability of recommendations
AI-Assisted Review: The platform uses natural language processing to analyze reports for key indicators of quality, helping reviewers quickly identify strong submissions while flagging areas needing closer human evaluation.
5. Comprehensive Analytics and Reporting
After candidates submit their security reports, the system generates detailed evaluation metrics:
Report Quality Scoring: Automated analysis evaluates report quality across dimensions like completeness, clarity, technical depth, and professionalism. Human reviewers can adjust scores and add detailed feedback.
Vulnerability Detection Rate: Track which vulnerabilities candidates identified versus what exists in the challenge environment, providing insight into thoroughness and security intuition.
Communication Skills Assessment: Since report writing is crucial in security roles, the system analyzes writing quality, structure, and the ability to explain complex technical issues to different audiences.
Comparative Analysis: Benchmarking against other candidates and historical performance data helps contextualize results. Organizations can see how candidates rank within their applicant pool and against industry standards.
Skill Mapping: The system maps performance to specific security competencies based on the types of vulnerabilities identified and the quality of analysis. Performance across different machine types reveals specialized expertise:
- Web app machine results indicate application security and OWASP Top 10 knowledge
- Network pentesting scores show infrastructure security and Active Directory expertise
- Reverse engineering performance reveals low-level analysis and malware research capabilities
This creates detailed skill profiles that align with job requirements, helping identify candidates who excel in needed areas.
Time Efficiency Metrics: Analysis of time spent on assessment and report quality helps identify candidates who work efficiently under pressure—a critical trait in security operations.
Advanced Features
Team-Based Assessments
For roles requiring collaboration, Parrot CTF Enterprise supports team challenges where multiple candidates work together. The system tracks individual contributions within team efforts, identifying both technical skills and collaboration abilities.
Continuous Candidate Pipelines
Organizations building talent pools can run ongoing challenges, allowing interested candidates to complete assessments at their convenience. The system maintains a ranked pool of pre-qualified candidates ready for immediate interviews when positions open.
Custom Scenario Builder
Security teams can recreate actual incidents from their environment as challenge scenarios. This allows assessment of candidates’ ability to handle the specific types of threats the organization faces.
Security and Compliance
The platform prioritizes data protection:
- End-to-end encryption for all candidate data
- GDPR and CCPA compliance with clear data retention policies
- Role-based access controls limiting who can view candidate information
- Audit trails for all system interactions
- Secure credential management and automatic cleanup of challenge environments
The Business Impact
Organizations using Parrot CTF Enterprise report significant improvements:
- Reduced Time-to-Hire: Automated processing and clear skill insights accelerate decision-making, reducing hiring cycles by 30-40%
- Better Quality of Hire: Practical skill assessment leads to better role fit and reduced early turnover
- Enhanced Candidate Experience: Technical candidates appreciate the opportunity to demonstrate skills over discussing hypotheticals
- Scalable Evaluation: Assess hundreds of candidates simultaneously without proportionally increasing recruiter workload

Leave a Reply